Hello, now we are going to install Squid 3.5.5-1 Release May 29, 2015. Before we continue, in previous i have explain in detail how to install squid proxy on Centos 6, it works on 64bit and 32bit architecture (http://www.angelimus.com/2015/07/how-to-create-elite-proxy.html).
Case : I have run VPS With Centos 6.6 64Bit with Squid Proxy Server 3.5.0.4, and i want to upgrade it to Squid Proxy Server 3.5.5-1.
Step 1 - Installing Squid Proxy Server 3.5.0.4
Lazy Mode Method = Install Repository, Install Squid 3.5.0.4, Configure Elite Proxy.
Now, we must add repository first, because old repository only serve Squid 3.1.10, i have create lazy mode, just type :
wget https://raw.githubusercontent.com/zaq111/bash/master/angelimus-install-squid-355.sh
chmod +x angelimus-install-squid-355.sh && sh angelimus-install-squid-355.sh
It's done, you have Elite Squid Proxy 3.5.0.4 installed on your VPS, now let's we costumize our squid.conf a little bit, type :
vi /etc/squid/squid.conf
Scroll down and find similar like below (i only show how to make public proxy, you can change below configuration into personal or authenthicated system, see previous tutorial about installing proxy at step 2 (How to Install Elite Proxy on Centos 6)
# And finally deny all other access to this proxy
http_access deny all
change http_access deny all into http_access allow all
Scroll down again and find
# Squid normally listens to port 3128
http_port 3128
change http_port 3128 into http_port 5678
save it by type :wq and type :
service squid restart
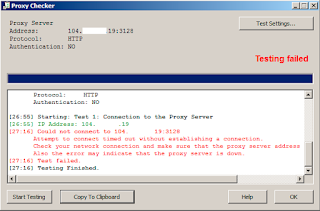
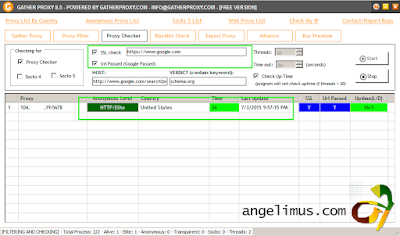
Now you are done, you have running squid, try it on your web browser.
Until this step you already done install squid 3.5.0.4, if you don't want to continue to next step, it's ok, you still can use your squid 3.5.0.4.
 |
| change ip address with your VPS IP Address |
Step 2 - Installing Squid Proxy Server
Manual Method = Upgrade Squid 3.5.0.4 to Squid 3.5.5-1.
Maybe there are a big question in your head, why not just install squid 3.5.5 rather than installing squid 3.5.0.4, well, i don't have a specific answer for that question, what i know is, if you start installing 3.5.0.4, it will not installed, because there are no dependancies, but maybe someone else know how to install 3.5.5-1 without install 3.5.0.4 first, i'm curious too :P
Ok, let's start. Just type :
service squid stop
[root@centos6 ~]# service squid stop
Stopping squid: ................ [ OK ]
squid -v | grep Squid
[root@centos6 ~]# squid -v | grep Squid
Squid Cache: Version 3.5.0.4
rpm -Uvh http://www1.ngtech.co.il/repo/centos/6/x86_64/squid-3.5.5-1.el6.x86_64.rpm
Preparing... ########################################### [100%]
1:squid ########################################### [100%]
squid.conf.documented is at /usr/share/squid-3.5.5/squid.conf.documented
It's done, now check your version again.
squid -v | grep Squid
[root@centos6 ~]# squid -v | grep Squid
Squid Cache: Version 3.5.5
Let's check our configuration, is it still same?
vi /etc/squid/squid.conf
In my VPS, there are NO CHANGES at all, it's upgraded succesfully.
Now let's start squid
service squid start
[root@centos6 ~]# service squid start
Starting squid: . [ OK ]
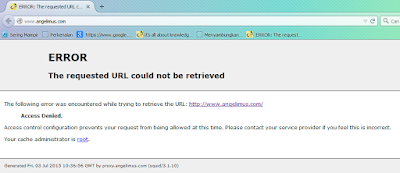
Let's try open angelimus.com
 |
| proxy not detected |
It's done, if you have some problem, please check my previous tutorial (How to Install Elite Proxy on Centos 6)
Thanks, and see you in next tutorial.